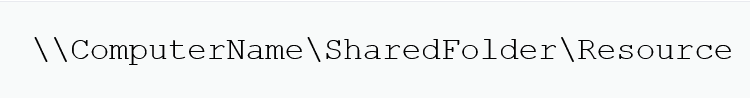AT A GLANCE

By Vicken Karaoghlanian, LENSEC Vice President of Product
WebRTC is growing as a new emerging technology. The LENSEC staff closely observes emerging technology trends for video streaming, including WebRTC. As it is proven useful, our engineers plan to adopt them in our product offerings. WebRTC has been in use since 2011 and is recently gaining traction as an internet communication tool for using common protocols. The applications using this technology include the following:
- Video Conferencing
- Social Media
- Interactive Online Gaming
- Peer-to-Peer (P2P) Data/File Transfer
- Secure Video Streaming
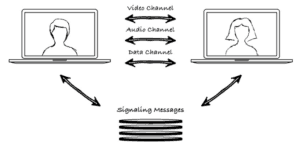
WebRTC is a free, open-source project that provides browsers and mobile applications with Real-Time Communications (RTC) capabilities via simple Application Programming Interfaces (API). Backed by big companies like Google, Microsoft, Mozilla Foundation, and Opera, the WebRTC project is driven by this mission in mind: To enable rich, high-quality RTC applications to be developed for the browser, mobile platforms, and IoT devices, and allow them all to communicate via a common set of protocols.
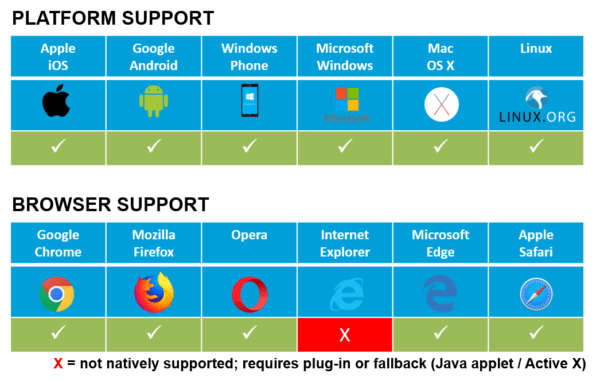
WebRTC is Becoming an HTML5 Standard
The project is currently being standardized by W3C, the World Wide Web Consortium. WebRTC is also being progressively becoming supported by all the major browser platforms. This interesting piece of technology is being rolled out as part of HTML5 specifications in modern web browsers.
In the past, LENSEC has leveraged different technology for video streaming in Perspective VMS®. The evolution of the PVMS streaming stack has followed this pattern over time:
The latest release of Perspective VMS® will leverage WebRTC without the use of any plug-ins. The architecture of WebRTC supports the streaming service in Perspective VMS®. PVMS relies on native JavaScript API to display video streams in the WebRTC equipped browser.
This communication protocol is one of the most secure ways to protect video streams. It will ensure your camera feed is not intercepted by another server. In addition, it will provide end-to-end encryption and P2P architecture.
IT staff only needs to open one port to get WebRTC to work. Use of this port is essential for the signalling process to communicate. The advantages of this technology are abundant.
Here are a few:
- No Browser Plugins Required
- Relies on Javascript and Browser-Native API to Enable Streaming
- Peer-to-Peer (P2P) Communication Means No Proxy Server is Needed
- Transfers Data, Audio, and Video
- Encrypted with AES-128
- Supports TCP/UDP Options
- Available in Modern Web Browsers
- Supports Multiple Codecs
WebRTC Improves Video Streaming Latency
In the surveillance world, experts can’t talk about video streaming without talking about latency. The good news is that low-latency is where WebRTC shines. The technology was designed from the ground up for real-time communication. Typically, streaming protocol variants such as HLS and DASH deliver streams with around 2 seconds latency. This is because HTTP-based protocols buffer chunks of data before sending it to the user. The chunk size plays significant role in introducing this latency.
WebRTC on the other hand uses UDP without the need to create data chunks, subsequently delivering stream packets almost immediately. In LENSEC’s testing labs, our engineers successfully streamed with latency below 500 milliseconds.
The disadvantages are minor, and expected in today’s technology environment. Here are a few worth considering:
- Internet Explorer is not Supported
- Older Browsers are not Supported
- WebRTC is Still Under Development
- Implementation Might Break with a Browser Update
The LENSEC development team is previewing WebRTC in the Perspective VMS® 3.5.0. Web Sockets, our current standard for video streaming, is still available and will be the default standard in our streaming services. However, we are evolving our video streaming technology stack from packet segmentation using Web Socket to WebRTC. Security integrator partners and end-users wanting to leverage WebRTC will be able to turn the feature on or off, depending on their needs.
WebRTC brings noteworthy features to Perspective VMS®. Here are a few we will achieve using WebRTC in PVMS:
- Ultra-Low Latency Streaming (Less Than 1 Second)
- Secure Video Stream with End-to-End Encryption
- Media is Protected from Interception
- H.264 Video Streaming on iPhones
Our partners and customers interested in previewing WebRTC in the latest version of WebRTC will have the option of enabling it in PVMS v3.5.0. Our technical support team and engineering staff can assist with this transition. Our team will be able to easily activate WebRTC or deactivate it, as needed. If our ongoing testing proves WebRTC to be dependable in Perspective VMS®, then it will become widely available in future product releases. For now, LENSEC is planning this to be a preview release. We will plan a more concrete integration in the future.
If you are interested in learning more about WebRTC and Perspective VMS®, please feel free to contact us. We’d like to talk with you and your team about how we can implement these technologies in your security environment.

By Nick Stigers, LENSEC Sr. Systems Support Engineer
It’s easy to see how lack of password management can open a vulnerability into your network. Cybersecurity experts don’t have to go far to demonstrate gaping holes in an enterprise network. When default passwords are in place, they can easily access IP cameras and other edge IP devices.
This is not even hacking, it’s simply accessing open IP devices. No hacking is required when a person can easily log into a camera using a manufacturer’s default password. This is easy to fix. Security managers and enterprise stakeholders should insist on proper security system protocols to never allow default passwords to be used.
When password vulnerabilities are demonstrated by cybersecurity experts, it’s easy to imagine how a person with ill intent and little skill could create huge disruptions in a businesses network. During the LENSEC Winter Conference in December, Jamie Bradford with Razberi Technologies expressed the importance of a strong password management plan.
Bradford says, “The bad actor can use default login credentials that are easily accessible to the public to gain access to IP devices such as security cameras, and gain access to exposed services, and find exploits in firmware. These exploits take advantage of a bug or vulnerability in order to cause unintended or unanticipated behavior. Once the camera is accessed, the bad actor can discover services exposed by the camera. We recommend turning off unnecessary services that may act as a backdoor for hackers or viruses. All of this can be avoided by practicing secure password management.”
The National Institute of Science and Technology (NIST) has been promoting new passwords security guidelines for federal agencies and contractors. The NIST guidelines point to long passphrases instead of complex passwords. The passphrase is a “memorized secret” that sequences text to authenticate identification. The NIST outlines their standards for federal agencies and contractors on securing digital identities in a recent report.
Keep Passwords Unique
It’s important to keep some uniqueness with passphrases and passwords. For passphrases, using a random series of words, non-English words, and avoiding commonly spoken phrases helps to keep the passphrase complex and unique. Individuals often develop passphrases based on commonly spoken phrases along with book, movie, and song titles. Password cracking algorithms have adapted now include these items in their routines. While the passphrase itself is strong and complex, the passphrase can be easily guessed due to the common use of the phrase.
Avoid performing password transformations when it is time to update a password. Transforming a password is a technique where the same basic password is continuously used with slight alterations. Passwords are often transformed by adjusting a digit or changing a letter character into a special character of similar appearance. An example is changing your password, “baloney” to “B@loney1.” This practice turns strong passwords into weak passwords since it creates predictable patterns.
All who use passwords know that managing them is difficult, and memorization of complex passwords doesn’t come easy. So, please consider some of the ideas we’ve presented to secure your cameras, IP devices, and network infrastructure. Any form of password management is better than none. Seize the day, and practice safe password management. Your security footprint will be more secure as a result.
Check with our professional LENSEC Technical Support Team. They have collective expertise to help you deploy Perspective VMS® and provide knowledge that will lend best practices to the security integrator and their customers. If our team can support you, please call us at +1 (713) 395-0800 + Option 1, or email us at [email protected].

LENSEC SUPPORT
by Keith Harris
When you have a few cameras, naming them in Perspective VMS® is almost an afterthought. You don’t really need a game plan for naming a limited number of cameras at one site. However, when you are working with hundreds or thousands of cameras in an enterprise-level, distributed security system, it helps to give some thought to your camera-naming method.
Perspective VMS® gives you the right tools to find your cameras and group them appropriately. We recommend developing a system for standardizing names of cameras at a site, or at multiple sites managed by PVMS. In fact, this same recommendation goes for labeling cables connecting your network architecture. If you do this on a new installation, you could be saving someone or even yourself multiple headaches in the future. This can speed up troubleshooting and maintenance going forward.
Site / Site Location / Description & Camera Type
When you are working with multiple sites, you can label a site with abbreviations or number the sites and make a legend for reference in the future. An example would be a school district with multiple properties. Each school could be numbered or abbreviated.
Smith School District: Barnes Elementary School
Abbv: SSD:BES
Site: 07
Each site location would likely have multiple buildings.
Main School Building: Kindergarten Hall
Abbv: KH
Main School Building: Gym/Cafeteria
Abbv: G/C
Portable Building 3: Mr. Jones 5th Grade Math Class
Abbv: P3
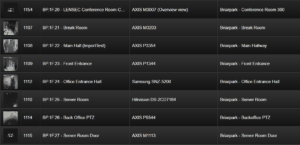
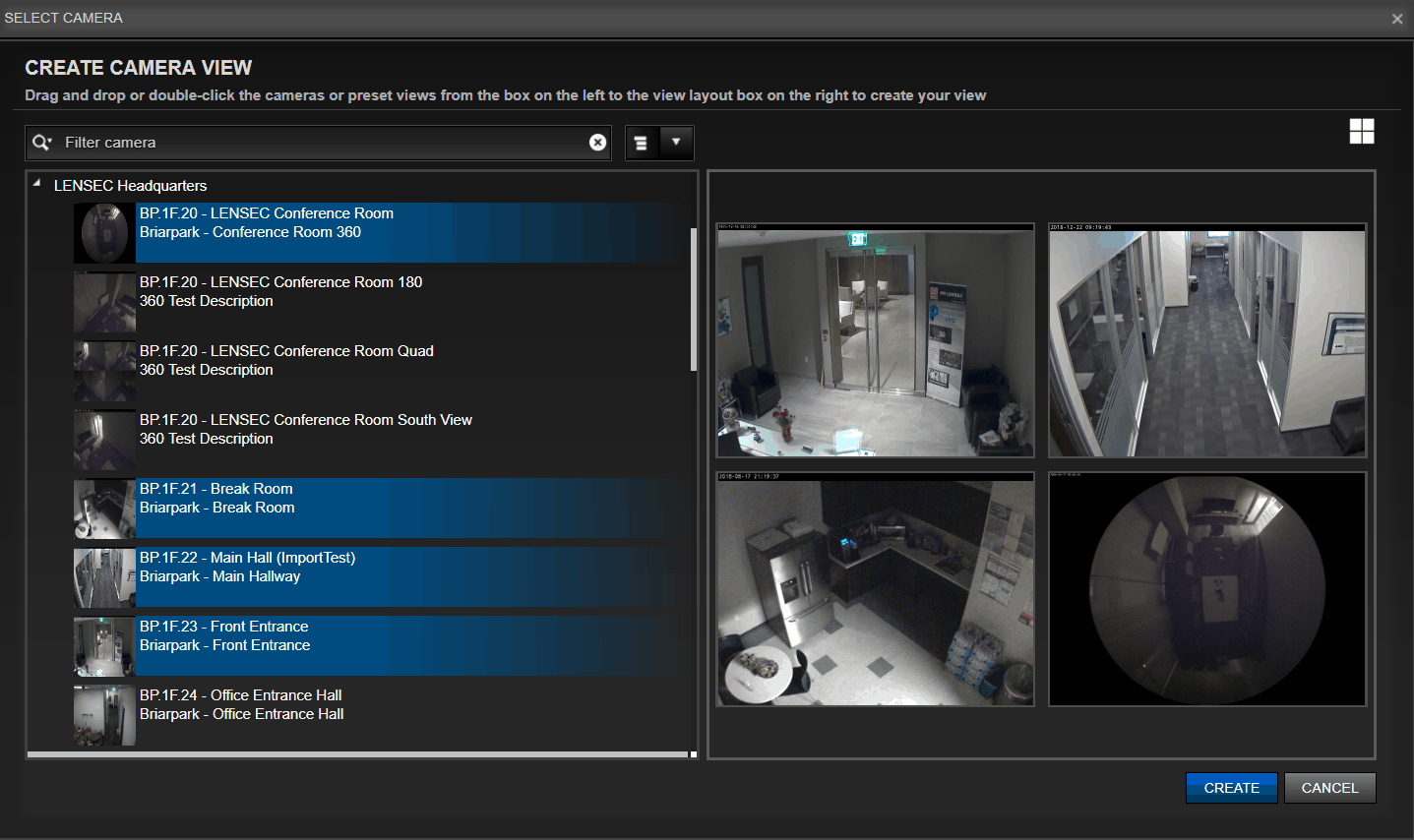
Once you decide on your naming method, stick to it and apply it uniforming throughout the enterprise. Make a spreadsheet with vital information and the naming convention, so best practices can be achieved moving forward. In PVMS, if you assign a numeric value to the camera name, they will be sorted in order. In this example, you’ll see the camera nomenclature for the LENSEC office in Houston, TX.
PVMS is designed to filter cameras, and sort them by name. This helps when you must drill down to a particular camera or group of cameras.
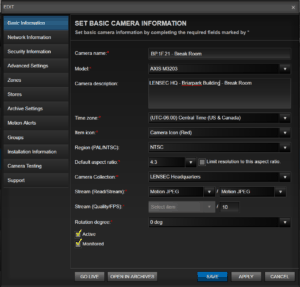
When you are editing camera information, you have an option to name the camera as you choose. Putting the camera make and model is required, as this will help you later when you need to gather details about a camera for maintenance or troubleshooting.
A helpful field is also the camera description. This can relate to a specific location in the building, such as a room number or building wing. This information becomes useful when searching throughout PVMS. By standardizing names and descriptions for the cameras, you’ve added metadata that is searchable using the global search tool, or selecting cameras for the camera view or archive modules.
In the example seen here for creating a camera view, you can see the naming convention of “BP.1F.20.” But, you can also see the cameras description, “Briarpark – Conference Room 360.” This information is pulled directly from the information we entered into the “Set Basic Camera Information” Dialog Box. As we described, the camera information is searchable from the global search tool. This improves the user experience, turning the information into metadata, and therefore searchable from the database.
Labeling Cameras, Devices, and Network Cables
If you are labeling cables, a best practice that experts recommend, use the same nomenclature that you are using for your cameras. While there is no comprehensive standard that is mandated for labeling cables, bid specs on certain jobs might require it. Certainly, the complexity of the job might make the ongoing maintenance and support of the security system easier in the future.
LENSEC experts recommend the following standard practices:
- Use Permanent Labels That are Clearly Printed, Durable, and Avoid Fading
- Use Printed Labels (not Hand Written) with Legible Text, Large Enough to Read
- Label Network Cabling at Both Ends and Common Access Points
- Use a Standard Camera Naming and Labeling Format
- Apply Labels the Same Way Throughout the Enterprise
- Make a Master Legend to be Used in the Future to Decipher Camera and Label Nomenclature
Placing a label on cameras and IP devices would also be a big help. If a cable ever gets removed or replaced without a label, it could be very helpful to have an info sticker right on the device. By using these best practices during installation and while maintaining a project throughout its life cycle, the security integrator will make their job easier and their customer happier.
If you need assistance with best practices on camera nomenclature, you can review our tutorial on the LENSEC website. Also, feel free contact us by email or phone. You may email our technical service team at [email protected]. Call us by phone at (713) 395-0800 + Option 1.

Partner Focus
LENSEC Regional Team Introductions
by Keith Harris
LENSEC is adding to our regional management team around the globe. Here are a few of the professionals we have covering relationships with partners and manufacturer reps. Our staff is comprised of physical security experts who interface with partners and their customers. They bring solid expertise in deployment solutions using Perspective VMS®.
Bob Brown is LENSEC’s Regional Sales Manager in the Midwestern United States. Bob has over 20 years of physical security experience. He has worked in sales and account management for numerous integrated security and life safety companies. Bob also has extensive experience in building channel partners for security and asset protection hardware and software for many notable companies. A native of Central Ohio, Bob recently relocate to the Knoxville, Tennessee area with his family.
Mike Deakes is LENSEC’s Regional Sales Manager for the South-Central United States. He has a strong sales background in the government marketplace, with a focus on life safety, law enforcement, industrial, K-12 education, higher education, and healthcare. Mike was previously with LENSEC and is back with the company again, serving his territory from Austin, TX. Mike develops customer relationships and helps leaders to improve best practices in various markets.
Rabih Farah is the LENSEC Channel Partner Manager in Saudi Arabia. Rabih is an IT expert specialized in networking and physical security solutions. He has been working with IT integrators and vendors since 2005 and joined LENSEC last year. He graduated with his BE in computer and communications from Notre Dame University-Louaize in Lebanon. Rabih manages LENSEC partners in the Middle East and other global regions.
Neil Haley has recently joined LENSEC as an Inside Sales Representative. He is based in Pittsburgh, Pa and has a 20-year background in sales, working with customers in media, education, and security. Neil has his Master of Education from Duquesne University. As a former teacher who taught elementary and secondary education in Pennsylvania, Neil has an expertise in the education market. In addition, Neil is a digital marketing expert, helping people develop more presence on the internet and social media platforms.
Mostafa Kashtan is LENSEC’s Business Development Director in the Middle East and global regions. He graduated with a computer engineering degree from Beirut Arab University in Lebanon in 2006. Mostafa also has his MBA from Hult International Business School. An entrepreneur by nature, Mostafa likes the challenges in business situation, and he’s passionate about innovation in business development. Based in Saudi Arabia, Mostafa has represented LENSEC for over 5 years, developing customer relationships and establishing new business with partners and their customers.
Michael Trask manages the Northeast region of the United States for LENSEC. His focus is on partnership development and channel sales. Prior to joining LENSEC in 2018, Michael served as the national sales manager for a continuous cloud-based recording surveillance company and a regional sales manager for a surveillance and loss prevention company. Michael is based in Pittsburgh, PA.
Heather Wolf recently joined LENSEC as the Regional Sales Manager in the Southeast United Sates. Heather is dedicated to the principles of quality and strives for continuous improvement in customer satisfaction. She has a strong background in Life Safety, K-12, Higher Education, Health, and Construction. Heather is a native Floridian. She is looking forward to continuing mutually successful relationships with LENSEC’s existing partners and creating the same with new partners in the Southeast territory.
Of course, LENSEC has an active support staff and sales engineers that do plenty of work with our partners and customers as well. These skilled professionals have a significant amount of cumulative expertise they lend to partners daily.
If you have questions about a project deployment or a use-case scenario for Perspective VMS®, our sales team is happy to respond and lend our expertise in any way we can. Please contact us by email at [email protected] or by phone at (713) 395-0800.

Perspective VMS® Product Feature
PVMS Archive Stores
by Keith Harris
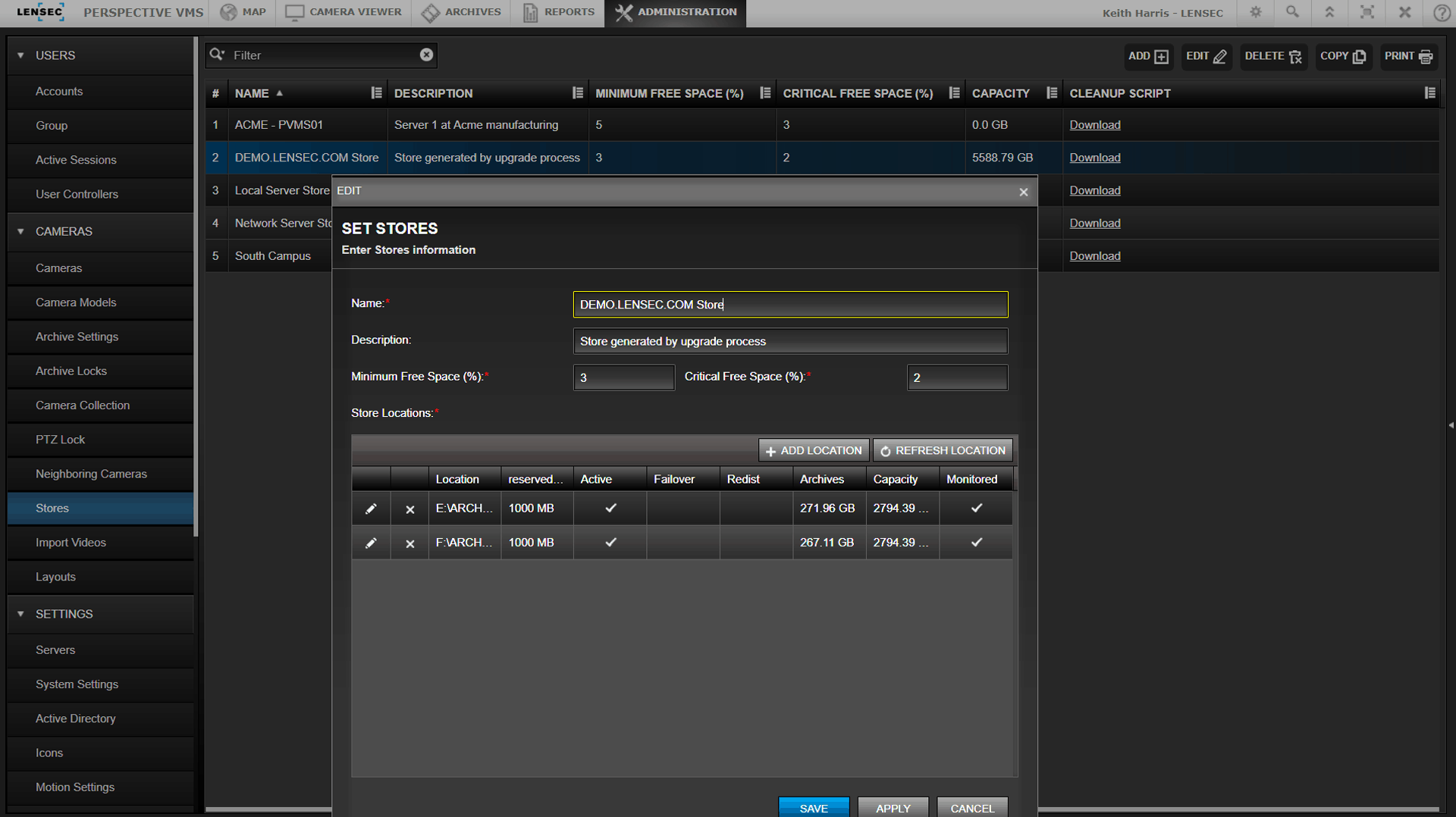
Archive Stores in Perspective VMS® provide the ability to dynamically store recorded video across one or multiple drive volumes. Archive stores are the locations for storage of archived video. These location paths can be combined to a store for dynamic distribution and balancing of archive files.
Storage can reside on your network or on local hard drive space. PVMS gives the administrator the ability to designate how much storage space to use on an available server or storage drive. PVMS is cloud-ready and may be configured for cloud storage in circumstances using the right network applications.
The benefit of an archive store is PVMS will dynamically to decide where to place archives, choosing the optimal location within the available storage locations. This means stored video recordings will automatically be balanced across the available storage drives. This appears seamless to the end-user, meaning you won’t have to know where the archive recordings are stored to access them in Perspective VMS®.
When creating a store, PVMS allows you to define a percentage of minimum free space and critical free space. This is helpful to ensure you maintain enough room on a storage drive before you reach drive capacity. An email notification can be sent when you approach the critical free space capacity in all active and non-failover store locations.
When adding drives for archive stores, you can designate the amount of free space you would like to reserve per drive. Archive stores may be added to system drives or storage dedicated drives, as needed.
When configuring archive stores in PVMS, you can choose a UNC path for archive stores. UNC is an abbreviation for Universal Naming Convention. Microsoft also refers to this as a network path. Here is an example of what a UNC path looks like:
A local store looks a little different, using a drive letter to start the local path to an onboard hard drive. Here is what a local store looks like:
When you add multiple storage locations, PVMS takes on the task of automatically distributing the archived video across the designated archive store locations.
Another useful feature is available during camera setup. When you are configuring a camera in PVMS, you can choose which archive store the camera will be using. It is a good practice to match the archive store with the server that is responsible for PVMS archive service. But, that’s not your only choice.
An alternative method is to select a storage that is across the LAN/WAN. If you choose this method, make sure your LAN/WAN is configured appropriately.
If you want to learn more about Perspective VMS®, please reach out to our sales team by contacting us at [email protected] or call us at +1 (713) 395-0800.
Upcoming LENSEC Events
LENSEC PVMS Technical & Sales Training Dates
Houston, TX, USA
JANUARY TRAINING
TECHNICAL & SALES CERTIFICATION TRAINING
DATE:
January 17-18, 2019
LOCATION: LENSEC HQ
3151 Briarpark Dr., Suite #125,
Houston, TX 77042
SALES ONLINE TRAINING
DATE:
January 29, 2019
LOCATION:
Online via Live Webinar
ADDITIONAL TRAINING DATES
IN HOUSTON & REGIONAL LOCATIONS
THROUGHOUT THE YEAR
LENSEC Headquarters
3151 Briarpark Drive, Suite 125
Houston, TX 77042 United States
LENSEC.com | +1 (713) 395-0800
Contact Us for a PVMS
Sales Demonstration or
Free 30-Day Software Trial