
By: Keith Harris
At LENSEC, we talk a lot about how to unify the security footprint. This includes bringing many different pieces of the security puzzle together, consolidating independent pieces of software and hardware to strengthen the entire physical security deployment.
LENSEC manufactures Perspective VMS® enterprise video management software. We strive to enhance our product by ensuring that it works well with security software and hardware manufactured by other companies in the industry.
The goal of doing this is to make software easier for the end-user to use. If the user can accomplish functions of various security tasks within the video management software, then it avoids the need to jump between software to accomplish basic tasks.
For LENSEC, this requires partnering with security technology companies and integrating software products. An example of this is enabling Perspective VMS® to pull alerts from an access control software, notify key users about activity, and leveraging reports to generate information about those alerts. Additionally, access control software might be able to use video captured by PVMS and play video related to specific alerts in their software.
While this is a general example, LENSEC software developers have identified several useful integration capabilities that end-users or security integrators can employ to strengthen the physical security footprint.
In a recent webinar for new and potential partners, I spoke about several considerations and best practices they might consider when planning a deployment an integrated solution for a unified security project.
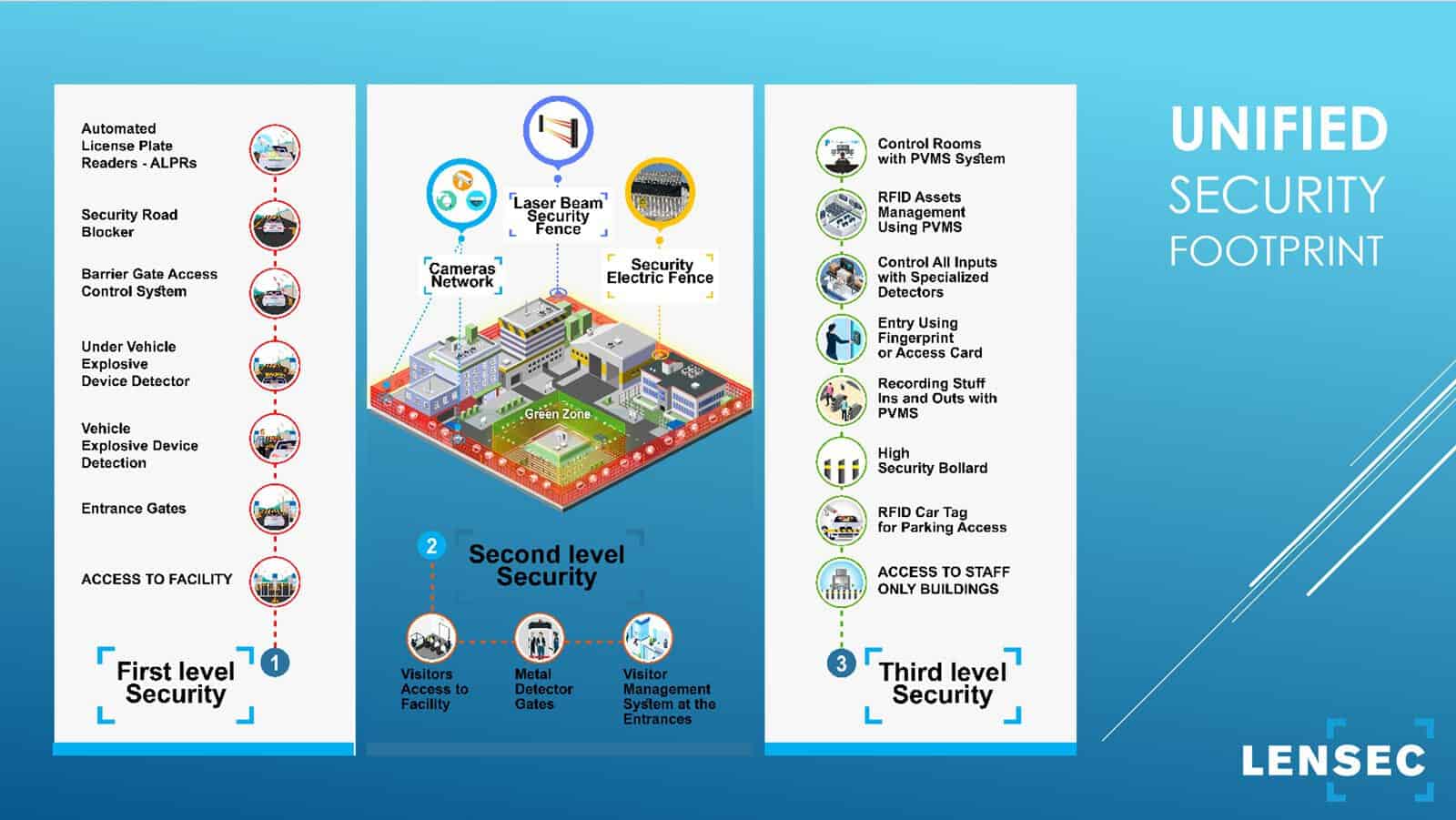
Planning the Project
When you’re looking at the integrated security footprint, you must consider how you want to plan the project. This starts with an evaluation. This could be right after you’ve met with the customer and discussed their ideas about what they are wanting to accomplish. You must evaluate the project to see if it is something you can accomplish. Is your team qualified to perform the job?
Part of planning the project is assessing the risk involved. This could be your risk assumed by taking on the job or it could be the risk you identify on behalf of your customer. When you go on-site for a survey of the potential project, you get a good look at their vulnerabilities. They may even be unaware the vulnerabilities exist. But, you may be able to provide insight into risks they have not considered.
You want to help them decide how they should deploy their security system. This could be recommending camera placement, identifying access control reader locations, or even suggesting the addition of lighting in a parking lot to prevent vandalism or theft. If the customer has plans for advanced integration, such as asset management or fleet security management, then you need to consider if you have the right resources to accomplish the project.
When you are helping the customer plan out the project, you may have recommendations that are new to them or that they haven’t considered. Partnering with LENSEC can help you with determining valid solutions for potential projects. LENSEC has over twenty years’ experience in the physical security industry. Some LENSEC history includes time as a systems integrator. We have people still on our team from that time. Some of our former project managers are now solutions engineers or application experts. These professionals can bring ideas into play that are seriously helpful for your customers.
Part of the job of planning the project includes keeping the stakeholders informed. You must be sure that important parties are updated on parts of the project that impact their area of influence. If you don’t know, ask who has a stake in the project early in your planning. It’s never good when an important stakeholder gets involved late in the planning process or after the project deployment has begun.
Potential Project Stakeholders
- Purchasing Department: decides on funding; rates project delivery criteria; and determines contractual agreements
- Campus Security Police: determines hardware placement; oversees security footprint management; and sets criteria for security system expectations
- IT Department: determines network architecture and infrastructure; sets guidelines for incorporating system into the network; and determines network security team
- Compliance Personnel: assess the risk involved and evaluates compliance with privacy laws
- Administration: reports to governing board or organization leadership
Software Integration
When an integrator is putting together the plan for their customer, they must ask specific questions to investigate the needs. Here is where a deep level of understanding the project comes into play. Many times, the customer will know what they want to accomplish, but they probably don’t understand how to get the desired end-result.
The integrator’s job is to put together a puzzle made of security solutions that achieve the desired result. In today’s technical culture, there are many disparate options available. But, the smart integrator will work to unify the security enterprise and design the systems of this security puzzle with interactive features, making the customer’s job easier.
The engineering team at LENSEC understands this need and is working to provide an integration capability in Perspective VMS®. The team is working to develop a world-class video management software that leverages a web application, avoiding a thick client software platform.
Choosing software that already is integrated with security solutions, such as access control systems, assets management systems, or building integration systems, is imperative. It’s important because enterprise-level software meets customer needs. When these disparate software management products can work in unison, life is easier for the end-user.
Hardware Integration
IP Device integration also helps provide solutions that can be beneficial to the security footprint. Engineers at LENSEC have identified hardware that works well with Perspective VMS® for a variety of use-case scenarios. Our team has developed solutions using common off-the-shelf (COTS) hardware, meeting a specific need and application requirement.
Our engineers are prepared to recommend solutions for fleet security management, for example. This leverages onboard, rugged video servers, vehicle-mounted IP cameras, and a variety of additional equipment that interfaces with the vehicle. Our design can deliver video and metadata to central data storage via Wi-Fi connections at the fleet depot. Now the transportation department can bring video and vehicle data under the security footprint for an entire enterprise.
In another example, our engineers devised a solution for the remote solar deployment of surveillance equipment. The stand-alone surveillance solution can operate in areas where there is no infrastructure supporting the equipment. This scenario is useful for oil & gas well sites. These sites require monitoring, though they are in remote locations with very limited infrastructure. Our engineers put together a solution that allows the end-user to log into the NVR remotely, monitor the site, or even receive notifications when activity is detected. This keeps the oil & gas companies from deploying personnel to check sites unless problems are detected. As a result, the company spends less time and money on their monitoring efforts.
Workflows
Our engineers have integrated hardware solutions for drone video, building systems, security gates, video analytics, RFID asset tracking, and much more. In many of these solutions, project engineers are leveraging workflows in PVMS. This is a business logic capability that uses ‘If-This-Then-That’ logic to trigger certain actions in the software based on events or alerts. For example, when a vehicle pulls up to a security gate, a workflow can be created to use data and third-party software to recognize an RFID signal and trigger the gate to open based on the signal received.
Summary
These are just a few examples of many solutions our engineers are designing to meet customer needs. Our team is working hard to develop solutions that work well with Perspective VMS in an enterprise security footprint. If you have questions for our team about solutions, please reach out and let us know.

