AT A GLANCE
THREATS: Dealing with Cybersecurity Threats for the Physical Security
SUPPORT: Planning Networks to Leverage PVMS Built-In Security
PRODUCT: PVMS Offers Built-in Security Protection
SURVEILLANCE: Avoiding Pitfalls in Emerging Surveillance
The LENSEC Perspective Newsletter July 2018
Dealing with Cybersecurity Threats for Physical Security Industry

There is no doubt that cybersecurity is having a substantial impact on businesses at all levels. The physical security industry is no different. But, where does the security integrator start to protect his business and the assets of his customer? Just knowing where to begin is daunting.
In the industry we’ve seen global scale cyber-attacks affecting hundreds of thousands of computers and IP devices in hundreds of countries. Everyone is impacted in some form or fashion by this growing threat. Ransomware attacks, denial of service (DDoS) attacks, hardware vulnerabilities, and back doors installed in IP devices just begin to scratch the surface of the lengths perpetrators go to hack into systems and steal data.

Recently, Tom Curtin with REPWORKS hosted a webinar sponsored by SIA, the Security Industry Association. Curtin is a certified expert in cybersecurity. He tells us that many well-known brands have experienced equipment hacks since 2013. REPWORKS is a LENSEC partner, providing representation for security integrators in the Northeastern United States.
Tom says, “Regardless of the device or manufacturer, there is no truly un-hackable device. Some of these companies have gone a long way to secure their products; some have created hardening guides; and, others have created standards and frameworks to protect their devices. We see a lot of company marketing materials that says, ‘we are un-hackable.’ That is not at all true.”
Best Practices
Curtin recommends going the extra mile to understand equipment and software vulnerabilities. Protect your reputation as a security integrator and provide the protection for your customer. It builds loyalty and satisfaction going forward. Here are a few simple tips that go a long way in defending your systems and those belonging to your customers:
- Keeping your computer antivirus updated is a simple task to improve protection.
- Computer updates are necessary to defend against hacks in the operating system.
- Updating firmware patches for IP devices is important to defend against cyber-attack to edge devices, such as cameras, printers, etc.
- Keep your backup files offsite to avoid ransomware snooping on shared drives.
- Update the firmware patch for your wireless router due to recent vulnerabilities in the WPA2 security encryption for WiFi access.
- Use strong, unique passwords for your network and IP devices and change them on a regular schedule.
- Hardening your equipment by disabling unused services will make it more difficult for hackers to get in.
- Bind MAC addresses and disable unused ports on network switches.
- Use Next-Generation Antivirus on your servers to provide superior protection against infiltration by hackers.
- Control network access by limiting the number of people authorized to use the security system network.
- Use 802.1x for your network protocol, requiring devices to authenticate before they can access the network and prevents unauthorized devices from tapping into the switch.
Cybersecurity Terminology
There are a lot of cybersecurity terms being used out there. Some can be confusing. For example, ransomware is a malicious worm that can move through your system of its own volition, encrypting your files as you go. The bad guy then holds your computer hostage, demanding a payment in bitcoin to release your computer data. Curtin says, “It would be ideal to not get infected, but if you do, the FBI tells us, ‘don’t to pay the ransom.’ There is no guarantee you’ll get your data back. More than likely, you won’t be able to break the encryption.”
Malware is an umbrella term that describes many typed of damaging software. Ransomware, trojan horses, and worms all fall under the umbrella of malware. Take some time to educate yourself on cybersecurity terms and best practices in defensive techniques.
The Responsibility of Risk
When an attack occurs, many parties become involved due to the risk responsibility. One might wonder who bears the burden of risk. Curtin explains the security installer is first in line to be held responsible, once an attack is implemented. This is because they are on the front line, recommending the manufacturer’s equipment and software.
Curtin addresses the security integrator and the risk they accept, saying “If you install software or hardware that is known to be vulnerable, that puts your customer at risk because you’re reducing their security posture. It puts you at risk, because when the customer gets angry, you’ll be the first person they go after, and then the manufacturer is up at the top of the chain. So, I would say the integrator has the most risk and is straight in the middle.” Tom recommends security installers to vet out their manufacturers by researching their equipment and software to identify potential risk before they choose it on behalf of their customers.
Protect Yourself
When you go to your customer sites and connect to their network, protect yourself by running antivirus on your computer. Tom tells us, “You don’t know what threats might be waiting for you within their network. You can keep from transporting their viruses to your network.”
There are certain things you should do to protect your liability. It’s also important to scan your network for vulnerabilities. Curtin recommends, “Once a month run a vulnerability scanner on your network – all of your computers. This will let you know if there are common vulnerabilities in your network.” Scanning your network regularly protects your customer and your reputation as a security integrator.
You can even consider insurance coverage for cyber liability. This protects you and your customer from the liability that comes with a cyber-attack.
If you want to see this webinar for yourself, here is the link to the SIA Webinar: Dealing With Cybersecurity Threats, featuring Tom Curtin with REPWORKS.
LINK: https://www.securityindustry.org/webinar/webinar-dealing-with-cyber-security-threats/
Look for additional information in this newsletter for information about LENSEC’s recommendations for securing your network environment when implementing Perspective VMS®.
LENSEC Tech Support Solution
Planning Networks to Leverage Perspective VMS® Built-In Security
Perspective VMS® Product Feature
PVMS Offers Built-in Cybersecurity Protection


Perspective VMS® is a secure software, ready with encryption that protects the entire security system. There are various levels of network setup recommended by LENSEC’s PVMS product experts. Below, we describe four typical setups that security integrators may use to build a network architecture. The differences described will vary, depending on the level of security needed by the end-user’s enterprise.
Network security is added using SSL (Secure Socket Layer) and WSS (WebSocket Secure) between the Perspective VMS® servers and the client workstations. Additionally, the edge devices may be setup on a subnet, communicating via the streaming service as a proxy. Overall, the advanced methods outlined here will add an extra layer of protection from hackers and harden the network architecture to prevent outside attacks.
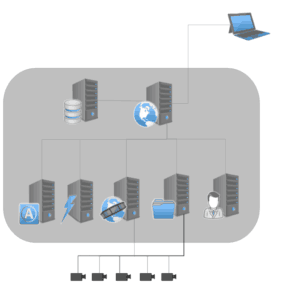
Basic Network Setup
- A typical Perspective VMS® solution consists of a web application, a database, and a series of services.
NOTE: These are often contained on a single server, represented here by a grey box.
- External connections exist from this server, connecting to the cameras and to the client PC (via web browser).
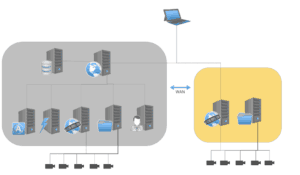
Distributed Network Setup
- In a distributed Perspective VMS® deployment across multiple sites, there remains a web application, a database, and a series of services. However, these services are split between multiple PCs or Servers, and offer multiple external connections.
- External connections exist from these servers, connecting to the cameras and to the client PC (via web browser and distributed streaming services).
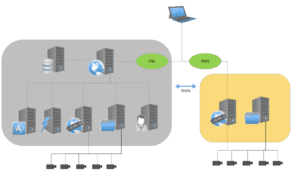
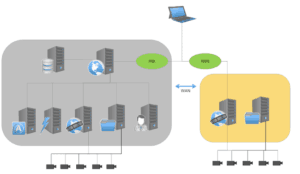
SSL & WSS Network Setup
- In this scenario, data transmitted between Perspective VMS® servers and the client PC can be secured using SSL and WSS.
- SSL (Secure Socket Layer) encrypts data between the client and the web application.
- WSS (WebSocket Secure) encrypts the video data streaming from the distributed servers.
Camera/Device Segregation via Proxy Network
- When using a proxy, the IP cameras and other edge devices can be segregated on their own subnet. The edge devices communicate to the client network via the streaming service only as a proxy.
- This segregation adds an additional layer of security to the network.
As a note, LENSEC technology partners, Bosch and Axis, manufacture cameras that offer SSL streaming. When HTTPS protection is enabled, data from the camera is encrypted. Now the video stream is protected from eavesdroppers and man-in-the-middle attacks.
If you have questions about deployment of security projects using network architecture as described here, please contact the LENSEC technical support team or physical security experts.
If integrator technicians need support, call (713) 395-0800 + Option “1” or email [email protected] for assistance.
LENSEC engineers have outlined several key protection mechanisms that are purpose-built with our enterprise-level video management software. Perspective VMS® comes packed with several security enhancements to help protect the system and the data contained within.
Configuration Encryption
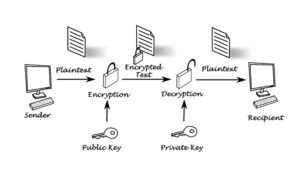
Out of the box, Perspective VMS® uses RSA encryption to code its configuration files. These files provide initial parameters and settings to the Perspective VMS® services. The files also contain some sensitive data such as usernames, passwords, and database connection information that the services need to function. RSA encryption uses a public encryption key and a private decryption key to help ensure that data stays private.
Protecting Web Traffic
Secure Socket Layers (SSL) can be enabled with Perspective VMS® to help protect the web traffic passing between the browser and the PVMS Web Server. Enabling SSL also secures traffic between the web server and other distributed servers within the network. SSL uses trusted certificates and, through a series of negotiation phases, creates a secured and encrypted connection.
The data contained within this secured connection is only visible to the hosts involved in the negotiating phases. This helps prevent Man in the Middle (MITM) attacks; an attack in which a third party interjects themselves between two hosts for the purposes of eavesdropping or impersonating one of the hosts.

Protecting Streaming Traffic
When using SSL, Perspective VMS® uses the Web Sockets Secure (WSS) protocol to help protect streaming traffic. WebSockets opens a real-time connection between devices communicating with each other. WSS is the communication protocol that is encapsulated within an SSL/TLS connection. WSS opens secure connections to the streaming services. This direct connection helps reduce the streaming data delivery time to the browser. WSS also helps further reduce the risk of MITM attacks as it creates a direct connection that’s encapsulated within an encrypted connection.

LENSEC Physical Security experts are ready to talk about the standards that the development team has adopted to make Perspective VMS® a secure tool in today’s physical security industry. The LENSEC team keeps your people and assets in mind when we are planning a successful project. The security of your data deserves our attention as well. We want to provide the best cybersecurity protection available within the scope of your physical security projects. Contact our team of experts if you have questions or would like demonstration of Perspective VMS®.
Contact: LENSEC Support Team
Email: [email protected]
Phone: (713) 395-0800 + Option “1”
Avoiding Pitfalls of Emerging Surveillance Systems

When the security integrator and end-users are considering surveillance systems, there is a great deal of complexity to consider. The average end-user probably doesn’t know where to begin, or where to focus their attention as they put together a solution for their business or organization. Security integrators can help, but the myriad of choices con be complicated.
Razberi Technologies is a LENSEC technology partners, and their experts tell us that complexity doesn’t have to equal complicated. Sometimes there is a simple solution to fix a complicated problem. The Razberi team prides themselves in manufacturing cutting edge surveillance solutions that are built to be reliable, cybersecurity, and network-optimized.
Recently, Razberi hosted a webinar on how to avoid the pitfalls of emerging surveillance systems. Stephen Schwartz, VP of Product Development, and Jamie Bradford, Director of Sales Engineering, talked with customers about different solutions and what to look for when evaluating surveillance systems.
Everyone expects the demand for network-connected devices to increase dramatically in the coming years. Bandwidth requirements to keep up with the expanding needs are also taxing businesses trying to keep up with demand.
The complexity issue generates the need for easy, reliable, and low-cost of hardware ownership and deployment. The lowest cost devices can be more expensive more in the long run than equipment that is properly designed to remain secure while optimizing its network usage. Razberi recommends a holistic, layered approach, using open systems.

Existing System Challenges
When using existing infrastructure employing centralized or distributed architecture, Bradford tells us each security project has its own challenges. When end-users have legacy equipment or analog cameras switching to encoders, Bradford says, “That introduces complexity, and could potentially offer vulnerabilities with legacy hardware.” Integrating existing technology into a new or refreshed system deployment will require proper planning to ensure the equipment is appropriate for achieving the planned results (i.e. – better resolution, protected endpoints, etc.).
Customers might need to adapt systems to meet new standards and requirements. Working with a knowledgeable and reputable integrator will help the customer understand when a solution using legacy equipment doesn’t make sense and produces an inefficient end-result.
Schwartz says, “You need a way to prevent cybersecurity threats from the edge with one hammer, not trying to keep track of problems in a cobbled together solution.” The integrator should suggest using an advanced endpoint antivirus and malware platform that are AI-based and do not require constant updates. This solution will keep up with the threats as they occur.
Scalability
Customers often tell the security integrator, “This is what I need to today, but I want to be able to plan for what I’m going to need tomorrow.” This need to scale can show in the need for data throughput from cameras sending higher resolution images over the network. We also see a need for scaling the number of network ports over time. Once ports are used up, adding additional cameras also means adding additional port capability.
Storage becomes a big concern as well. Bradford says, “We meet with state and local government, and we see the regulations that are put upon them, especially law enforcement, the longevity of that storage is needed for two to three years.”
That can create a need for massive storage on the network, requiring much more storage than most customers plan to purchase, especially when you need video captured at a high quality and frame rate. Careful evaluation of scalability becomes important if a customer needs a high-resolution camera, or adds services such as video analytics that add stress to an existing network. Bradford tells us, “There is a trade-off of capability due to network restraints. A lot of customers say, ‘I need that high-quality forensics at the edge, but I just don’t have the pipes to do it. That’s a big trade-off and it could be a pitfall.”
Investment in equipment that will optimize the network without compromising quality is an important consideration. Customers can avoid this pitfall by choosing equipment and software that includes health monitoring. Razberi has solutions for this, and LENSEC also includes a health monitoring solution in Perspective VMS®. Monitoring your network can identify issues before they become real problems. Having regular monitoring reports can identify equipment issues before you discover outages at the worst possible time – post-incident.
It’s also important for customers to know the value of open-architecture platforms. Many companies sell systems that are proprietary in nature. This means, they don’t work will with other company’s equipment. When the customer’s technology supports open platform, the scalability improves over time. Schwartz says, “I actually appreciate VMS providers that allow [Razberi] integrate right into their video security management systems.” Perspective VMS® has an open platform and Razberi integration that allows for future scalability.

Evolving Market Needs
If the security integrator and their customer don’t pay attention to emerging market trends, they are facing a potential pitfall. Video analytics are making an impact on the security market by allowing customers to implement smart alerts for facial recognition, behavior monitoring, and remote site monitoring. Schwartz explains, “In the event of theft, particularly in the energy sector, we’re seeing a lot of need for that edge processing. This helps predict abnormal behavior to help prevent people breaking in and stealing copper, for example.” LENSEC has a solar solution that they can recommend for remote sites without physical infrastructure, such as buildings, existing power, and more.
Cybersecurity risk is trending upward still. According to a study by Accenture over eight years, the average annual number of security breaches has increased by over 27%. Schwartz says, “That is actually stealing data from you and using it in some sort of nefarious way. Just a simple malware attack is extremely costly. It can take you over a month or more to resolve that. In some cases, we’ve seen where cameras or endpoints got infected, and they couldn’t reset the factory defaults to get rid of it, so they had to throw away the equipment.”
Technology is advancing in great strides to be able to provide better equipment at the edge. Not only rugged equipment, but also edge protection from cyber or physical attacks becomes essential.
When rugged equipment is used in certain environments, integrators and customers must decide if they are storing video and data processing at the edge or are they backhauling the information to a centralized management location. Current technology allows for data streaming using a limited bandwidth backhaul, such as LTE or satellite transmission. Bradford says, “They need to remote monitor to know the health of those signals way out in those rugged environments. Generalized surveillance is not going to serve this environment. Lack of edge security and hardening of endpoints create a pitfall that integrators and customers need to learn about.”
Pitfalls Require Market Ready Solutions
To summarize, here are key solutions that help the integrator and customer avoid pitfalls in today’s emerging security market.
Emerging Security Solutions:
- Open Platforms for Easy Integration
- Quick & Easy Deployment
- Reliable Equipment & Software Protects Reputation & Credibility (Integrator and Customer)
- Lower Total Cost of Ownership (TCO)
- Automate Cybersecurity with Machine Learning
- Stay Ahead of Increasing Complexity (i.e. – Regulations, Threats)
Razberi Technologies builds products and services that are right-sized for customers seeking network optimization without sacrificing video quality, protection from cyber-threats and end-point vulnerabilities, and hardware and cyber health monitoring. Pairing Razberi Technologies products with LENSEC’s enterprise-level software, Perspective VMS® makes good sense. Razberi and LENSEC work together to provide a lower cost solution that advances on that need to also provide quality solutions for today’s complex security environment.
Razberi Technologies CameraDefense™ is a key example of edge protection. This is embedded within the Razberi platform. CameraDefense™ automates industry best practices and standards at the network edge. Schwartz says, “When we first developed the product, our goal was to apply world-class policies that could protect cameras and endpoints at the edge in less than four minutes.”
CameraDefense™ Capabilities:
- Device Binding – Port traffic is limited to known MAC addresses
- Firewall – Protect system from common service attacks
- Whitelist – Restrict traffic to known authorized networks
- Internet Protection – When an internet connection is necessary, added protection is available
- Password Protection – identifies cameras with known default or weak passwords
We’ve only covered a brief summary of the information Schwartz and Bradford talked about in the Razberi webinar on Avoiding Pitfalls in Emerging Surveillance Systems. You can watch the on-demand webinar on the Razberi website. If you have questions about Perspective VMS® and solutions paired with Razberi hardware, please contact us for more information.
LENSEC Headquarters
3151 Briarpark Drive, Suite 125
Houston, TX 77042
LENSEC.com | (713) 395-0800
Contact Us for a PVMS
Sales Demonstration or
Free 30-Day Software Trial