AT A GLANCE
SUPPORT FEATURE
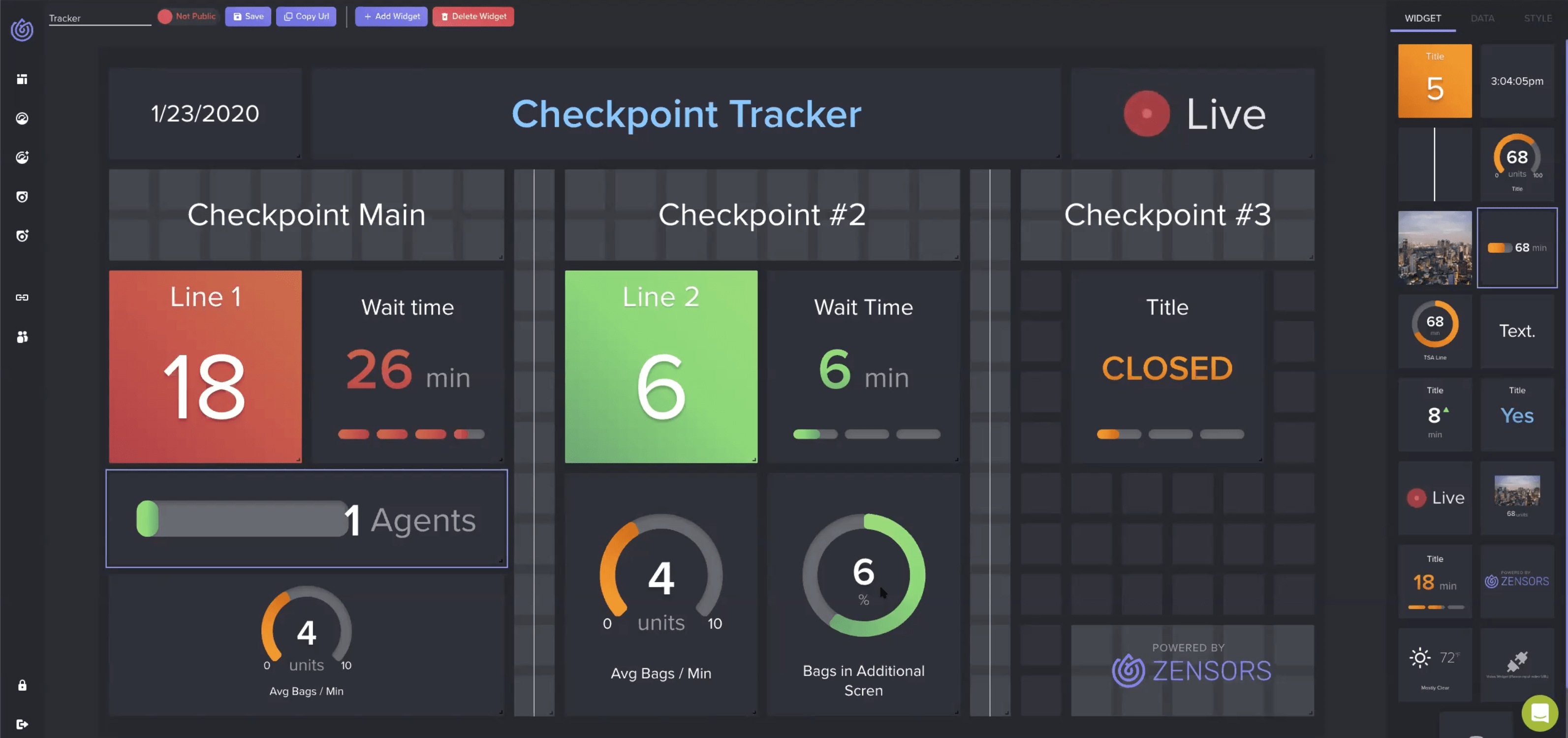
Bitrate & Camera Configuration
SUPPORT: EXTRACTIONS
Camera Viewer: Real-Time Extractions
PARTNER FOCUS
LENSEC Is Proud To Work With Partners Like Fidelis
PVMS HIGHLIGHT
Managing Door Events With PVMS & Integrated Access Control
IMPROVING RESPONSE TO COVID-19 WITH APPROPRIATE PHYSICAL SECURITY TOOLS
What a year 2020 has been. Everyone is seeing challenges. Whether business owners are implementing new cleaning protocols, developing social-distancing policies for the workplace, or learning how to approach their market in a new way, all are experiencing change at a rapid rate.
The security industry is no different. We are seeing rapid adjustments by technicians tasked with installing security equipment under new guidelines. VAR partner companies are prospecting and selling their services to end-user companies in different ways. We’re even seeing new technology in the market that addresses the new normal. This includes hardware such as cameras to detect elevated body temperatures in personnel, video analytic algorithms designed to detect compliance with face mask policies, and more.
At LENSEC, the team is adjusting to these challenges and facing them head-on. We are committed to keeping people safe and assets secure. In recent weeks, we’ve talked with experts from a variety of different industries. Experts from schools, healthcare administration, faith-based organizations, and retail corporations have shared best practices they’ve been working to get in place since COVID-19 came on the scene.
The reality is the challenges are forcing us all into considering whether previous practices are safe. At LENSEC, we are evaluating technology that can help companies remain secure and keep their personnel and customers safe.
VIDEO ANALYTICS
The team from LENSEC is looking to Video Analytics to help companies implement and enforce new policies put in place at businesses during the pandemic. Prevention is key in this matter. Using video security cameras, and analytic algorithms, company leaders can gain instant information on how many people are occupying space in key areas.
With the prevention of contact in mind, video analytics provides a social-distancing tool, ensuring personnel and customers are maintaining a standard of 6 feet between others in their area. Our partners providing video analytics have experience in developing algorithms that detect a variety of activities. One new technique is evaluating whether people are wearing face masks or not.
CONTACT TRACING
While contact tracing might be a controversial subject in the public forum, it can be an essential tool for some companies. A unified security footprint, including access control, video surveillance, and visitor management might be very helpful in certain environments to track the movement of people.
When a person has been identified as a risk for COVID-19, it becomes important to understand who that person has been in contact with. Forensic investigation of surveillance video and access control logs might lead to the discovery of potential contacts. Management would have more information available to make proper policies and procedures, helping to prevent the spread of the disease.
A good plan by an end-user company is enhanced by relevant technology and goes directly toward the goal of keeping people safe during a challenging time.
If you need assistance developing a plan for implementing technology to enhance a unified security footprint, contact the LENSEC team for more information. We are available to demonstrate existing technology or develop a new way to approach challenges in your workplace.

QUESTIONS ABOUT REOPENING ARE IMPORTANT FOR SCHOOLS
We all have questions about COVID-19 best practices when reopening businesses, bringing employees back to the office, and how we can best protect ourselves and those around us. School administrators have an especially tough job navigating the social-distancing culture we are now facing.
The pandemic has been going for several months now and school leaders are already shifting their focus. Administrators are considering how to prepare for reopening school facilities for the Fall. This is no easy job. Consider how a school with hundreds of students in close quarters can continue to operate under a pre-pandemic normal. It’s hard to imagine.
CHILDREN ARE SOCIAL CREATURES
Little kids are notably social. They can’t seem to keep their hands to themselves. When my kids were young, I believed they had extra arms just meant for touching me and everything around them. Curiosity and touching seem to go hand in hand for young children.
The older they get; it doesn’t get much better. Pre-teens and teenagers hate to be told what to do and seem to go out of their way to do the opposite. If Mom says don’t touch, Dad is likely to catch them red-handed. They are the proverbial “rebels without a clue.”
CDC GUIDANCE FOR SCHOOLS
While school administrators have a lot to consider, the Centers for Disease Control and Prevention is offering guidance. A simple tool that has been issued by the CDC is a decision tree for K-12 school administrators designed to assist them and provide links to resources as they navigate reopening schools during the COVID-19 pandemic.
The considerations are briefly covered on the CDC’s decision tree. Here are some issues administrators are tackling:
- Widespread COVID-19 testing may become a requirement in schools.
- Quick-read thermometers could become standard in classrooms and hallways.
- Schools may require students and staff temperature checks before they enter the school facility.
- Rigorous cleaning protocols and protective gear will become standard on school campuses.
- Administrators are contemplating procedures for people-tracing among those who test positive for COVID-19.
- Quarantine of infected students will affect parents and school personnel.
- Opening schools too early could expose students if the predicted second wave of disease returns in the Fall.
There are many businesses out there that want to help schools navigate this process. Entrepreneurs are not idle. They are thinking of tools and technology to help schools be successful in reopening. Just as many businesses shifted production to help create face masks, hand sanitizer, and ventilators, some companies are considering tools for helping schools find their next normal.
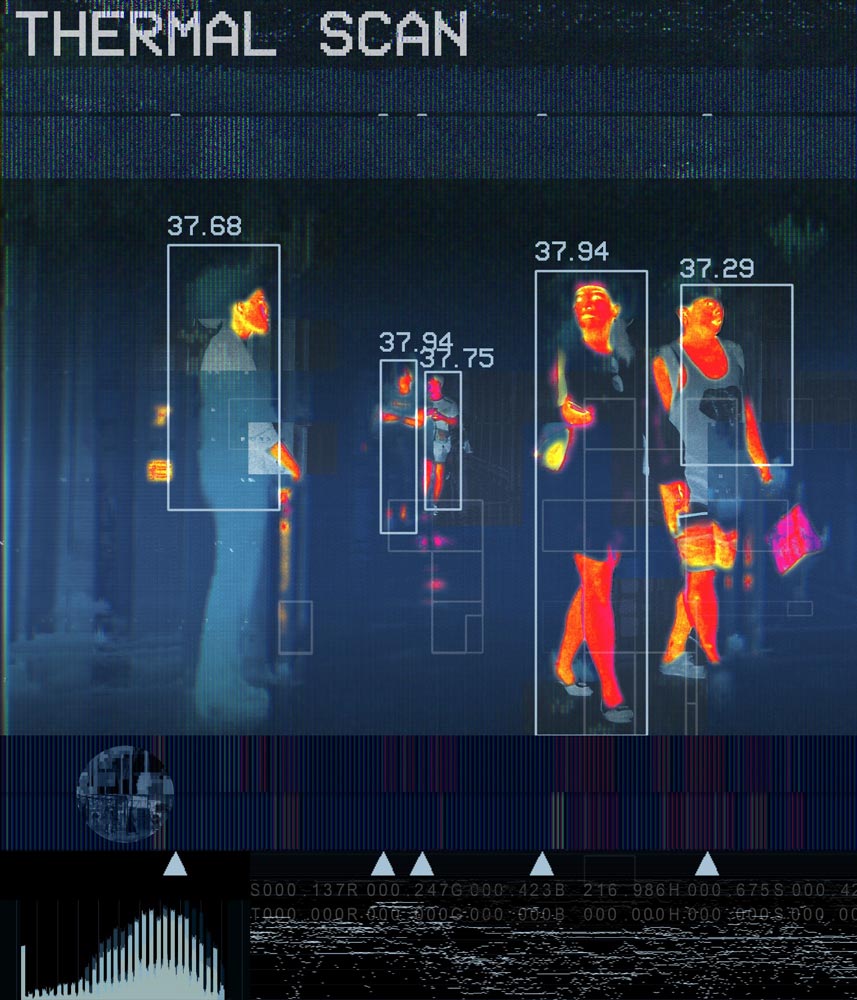
THERMAL CAMERAS FOR FEVER DETECTION
In the physical security industry, there has been much debate about cameras using sensors to detect people with fever. Many security experts wonder about the accuracy of the devices. Some companies marketing so-called “fever cameras” are being called out for making unproven or false claims.
The Food and Drug Administration regulates the use of telethermographic systems for health applications. This technology is appropriate for triage and converts infrared radiation into a body temperature measurement. The FDA issued guidance on the use of telethermographic systems for locations where thermometers might be in short supply, such as business, airports, schools, and more.
The debate regarding “Fever Cameras” continues around many products that businesses are marketing during the pandemic. School administrators must be cautious about implementing technology that hasn’t been thoroughly tested. Often when schools purchase technology, they must continue to use it for many years before funding for new technology becomes available. Making wise choices despite lack of knowledge is paramount.
Some say devices detecting pre-diagnostic temperatures can be helpful when used appropriately. Early triage of an infected person might prevent a lot of people from being exposed to the coronavirus.
VIDEO ANALYTICS AND WORKFLOWS FOR EARLY NOTIFICATION
When cameras or sensors generate a digital temperature, the information can become a Video Analytic. This is metadata associated with video evidence. The registered temperature can be compared with acceptable ranges and trigger alerts to personnel monitoring for anomalies. An early warning could be crucial in identifying an infected person and those people who might have made contact.
When using video analytics with enterprise-level video management software, advanced capabilities become available. LENSEC has a product that includes automated processes that can improve real-time awareness of behaviors and conditions. Perspective VMS® includes workflows that use “if-this-then-that” logic to generate notifications to personnel when pre-defined conditions occur. These tools may be used to improve early warning of personnel and prevent unwanted conditions.
The “Fever Camera” debate is just one example I’ve seen in my industry. Many other debates are just as relevant and important to consider. School administrators have their work cut out for them heading into summer. They will continue to monitor conditions, adjust, and readjust as the Fall semester arrives. I’m sure the landscape of the next normal will look very different than it does right now.

LENSEC SUPPORT
Bitrate and Camera Configuration
Choosing The Correct Codec, Resolution, And Video Quality
By: Bryce Capodieci
Editor’s Note: Over the next few newsletters, we will focus on a four-part feature series designed to help people understand the intricacies of camera configuration and bitrate usage. Here are the topics we have planned for this series:
- July 2020: Choosing The Correct Codec, Resolution, & Video Quality
- October 2020: Smart Camera Locations & Image Complexity
- January 2021: Camera Settings
- April 2021: Summary of Solutions
Part 1 of 4
When digital cameras first came out, they were all the rave. You could take pictures without fear of wasting film. You could also view the images immediately and delete the ones you didn’t want. You didn’t have to pay for film anymore, nor wait for your photos to be developed.
High Resolution & Quality
In today’s world, things are a little different. We all expect a high resolution and high quality in photos and video. The same is true in our security surveillance industry. We all expect to have the best possible video resolution and quality. But do you ever stop to think about what this high expectation requires?
When designing and configuring a video management solution, we must consider the bitrate, video compression type, and bandwidth components of the system. To predict the bitrate component, you need to understand what the camera is capturing. Here are a few key considerations:
- Scene Complexity
- Continuous Motion In The Scene
- Changing Light Over Time
DEFINITION: Bitrate
The website Encoding.com defined bitrate in their knowledge base. Here is there definition:
A video bitrate is the number of bits that are processed in a unit of time. Remember that 1 byte consists of 8 bits. Video data rates are given in bits per second. The data rate for a video file is the bitrate. So, a data rate specification for video content that runs at 1 megabyte per second would be given as a bitrate of 8 megabits per second (8 mbps).
Video Codecs & Bitrate
Another issue security manufacturers and integrators contend with is the use of legacy cameras that stream in Motion JPEG (MJPEG). Raw and uncompressed video has an extremely high bitrate. Consider upgrading those cameras to newer models that offer H.264 or H.265. When configuring cameras to stream in these newer codecs, it’s important to understand the image quality settings.
Most camera and video management software (VMS) manufacturers will provide streaming quality options such as high quality, medium-high quality, medium quality, medium-low quality, low quality, or a numbered scale. These scales do vary between manufacturers as far as distinguishing between levels and the range of the scale.
It’s not necessary to assume you should always select high quality on the scale. As the video quality increases, the bandwidth usage does as well. The best practice is to let the anticipated content of your video dictate the level of streaming quality. But first, let’s understand what video quality means.
What Is Video Quality?
The quality of the streaming video is not directly related to the resolution of the camera. You can compare two cameras side-by-side. Both cameras are 10MP cameras. The first 10MP camera (Camera A) is set to low video quality, whereas the second 10MP camera (Camera B) is set to medium-high video quality.
Let’s set up a few assumptions when we consider how the variables affect video quality:
- The frames per second (FPS) match
- The streaming codec is H.264
- The cameras are viewing the same scene
- The cameras are from the same manufacturer
Which video stream do you think will provide better details, and which one consumes more bandwidth? The answer should be obvious. Camera B provides the best image quality but has a higher bitrate, so it consumes more bandwidth. Camera A has a visibly lossy image but saves a considerable amount of bandwidth compared to camera B.
Therefore, if precise details are not required, and you only need to monitor activity, consider using a lower video quality to save on bandwidth utilization.

DEFINITION: Lossy
The TechTarget website provides a definition of lossy compression for us:
Lossy compression reduces a file by permanently eliminating certain information, especially redundant information. When the file is uncompressed, only a part of the original information is still there (although the user may not notice it). Lossy compression is generally used for video and sound, where a certain amount of information loss will not be detected by most users.

Pixels Matter
Resolution is based on the number of pixels in each target area. While streaming quality is based on the number of frames that are kept or removed from the video stream. The higher the video quality, the fewer frames are removed from the video stream. At a lower quality video stream, even at high resolution, the video will appear lossy. But in this case, the camera will be streaming at a considerably lower bandwidth.
Where Did My Frames Go?
Frames are removed so the video codec can reduce the bitrate. The codec determines which frames are redundant or unimportant and simply deletes those frames forever. As the number of frames of streaming video is reduced, the bitrate is also reduced. When selecting a low video quality, you are instructing the codec to remove as many of the redundant and unimportant frames as possible, thus giving you a lower bitrate. When selecting a high video quality, you are instructing the codec to be very selective in removing any frames. As more frames are kept, the bitrate increases.
Most camera manufacturers will set defaults at the medium video quality. It is also important to mention that most camera manufacturers use their version of the quantization scale. This makes comparing one manufacturer to another very difficult.
Video Quality: Good, Better, or Best
Determining which video quality is best for you is more subjective than scientific. It is mostly based on how much loss you are willing to accept. For example, in the case of a casino that monitors gaming tables, it’s best to have high video quality. This is because more frames of the video are kept, thus more detail streamed and captured. Offices, parking lots, and public venues are good candidates for medium-high to medium settings. In places where recognition isn’t important, but detection is; you can consider using medium-low to low video quality. Examples of these locations could be oil fields, warehouses, stairways, ski slopes, etc.
Improving Your Bitrate
The focus of this article is geared towards improving your bitrate. Except in cases of investigation where each frame is examined, the human eye won’t notice many differences between high quality and medium-high quality. IPVM reports that for the best tradeoff between best video quality versus compression, the sweet spot is medium video quality. The physical security experts at LENSEC normally recommend setting the video quality to medium-high.
There are still many factors to consider when attempting to reduce your bitrate usage. In the next newsletter, we will focus on how understanding image complexity affects your bitrate and how camera placement is an important consideration when trying to minimize your bitrate.

Editor’s Note: At LENSEC, we want to provide the best tools possible to our partners and Perspective VMS® end-users. We’re writing up technical guides for creating video extractions from surveillance video archives. Over the next few newsletters, we will focus on a four-part technical series designed to help with the key elements of video extractions. Here are the topics we have planned for this series:
- July 2020: Creating Real-Time Extractions
- October 2020: Locating Your Extracted Files
- January 2021: Creating Archive Video Extractions
- April 2021: Troubleshooting Real-Time Video Extractions
Part 1 of 4
Real-time video extractions enable users to record live video and extract it from Perspective VMS®. This can be done with or without motion or external trigger, by a simple one-click interface on any camera view. Extractions can be created in both the PVMS Camera Viewer Module and the Archive Module. This technical guide will explain the proper steps for creating real-time video extractions.
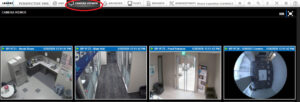
SINGLE CAMERA EXTRACTION
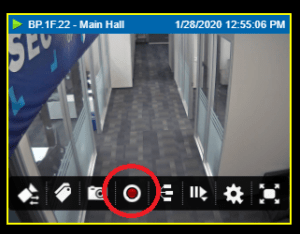
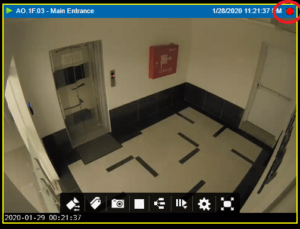
2. To extract real-time video, hover over the correct camera container. The camera overlay menu ribbon will appear at the bottom of the camera container. Click on the red ‘record video’ icon. ![]()
3. If you don’t see the red ‘record video’ icon , this means this camera isn’t set up for real-time extraction. To configure this feature in the administration module, a later article will cover ‘Troubleshooting Real-Time Extraction.’
Note: You must have permissions to configure this feature. Contact your PVMS administrator for support.
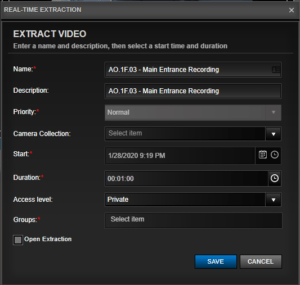
5. For your convenience, most of the fields are auto-filled with default information that you can reconfigure.
- Name: This field is auto-filled with the camera’s name. You can choose your own camera name.
- Description: This field is auto-filled with the camera’s name. You can choose your own description.
- Priority: The default setting is ‘Normal.’
- Camera Collection: You can select from the drop-down menu to add an optional camera collection with which to associate this extraction.
- Start: The start time appearing in this field is associated with when the real-time recording button was pressed.
- Duration: The default time is set for one minute. You can change this to any amount of time up to 24 hours. You can also select a preset time by pressing on the clock icon.

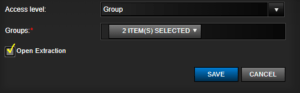
- Access Level: Default setting is ‘Private’, but you can choose the following permissions from the drop-down menu:
– Share: When ‘share’ is selected, only the PVMS users you select can view the extraction.
– Private: When ‘private’ is selected, only you can view the extraction.
– Group: When permissions are defined by the group(s), you select from the drop-down menu from the ‘Group’ field.
- Group: By default, ‘group’ is inactive. When ‘group’ is selected under ‘access level,’ you can choose the group(s) from the drop-down menu. One or several groups may be selected simultaneously. Continue clicking on the groups you wish to add. To remove a group, click it a second time to deselect it.
- Open Extraction: If the check box is checked, the image extraction drawer will slide open from the right sidebar automatically after clicking ‘SAVE’.
Note: It may take several minutes before your video is ready to view.
- Processing: While the video is being extracted, you will know the recording is in progress due to the flashing red recording icon in the top right of the camera viewer.
MULTI-CAMERA EXTRACTION
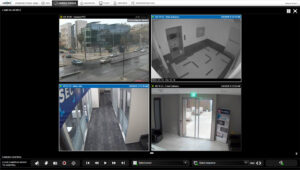
1. To create simultaneous extractions from several streaming videos, click on the black header of an individual video container within the Camera Viewer. When the header turns blue, it is selected. If you click it a second time, this deselects the video container; the blue header will revert to a black header. Repeat this process for each video container you wish to extract video. Note: In our example shown, we have selected two out of the four video containers to extract video.
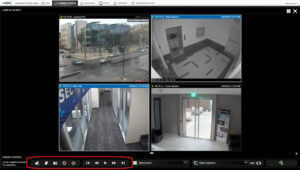
2. After the cameras are selected, navigate to the global camera control bar below the video containers and click on the red ‘record video’ icon ![]() .
.
3. After pressing the record button, please follow steps 4-5 from Single Camera Extraction, described previously in this article. Please be sure that real-time extractions are configured for each video container you select. To configure this feature in the administration module, a later article will cover ‘Troubleshooting Real-Time Extraction.’ If this feature is not configured for a video container, you will output an empty video file. The video thumbnail will display, “No Data Available.”
Note: You must have permissions to configure this feature. Contact your Perspective VMS admin for support.
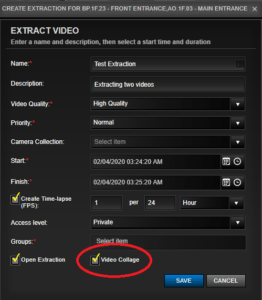
4. In addition to steps 4-5, you have two new features available to you:
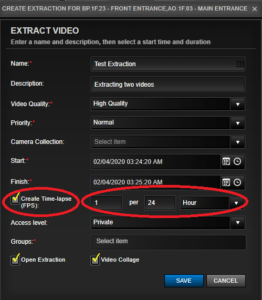
- Create Time-lapse (FPS)
- Video Collage
5. To create a time-lapse video, check the box. Then select the frequency of extraction. If done, click ‘SAVE’. In our case below, we have selected one frame (picture) for every 24 hours.
Note: You must make sure that the time-lapse frequency is within the Start and Finish time frame. Our configuration below of one frame per 24 hours would not work because the extraction between Start and Finish is only one minute.
7. If you checked ‘Open Extraction’, the extraction table will slide open from the right after you click ‘SAVE’. Otherwise, follow the instructions for Locating Your Extracted Files.
NOTE: The article ‘Locating Your Extracted Files’ is upcoming for Part 2 of this series.
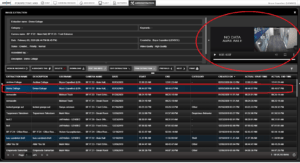
8. Once your extraction has loaded, highlight the extraction to view the details. In our example below, we extracted two videos. One of the cameras was not set up for video extraction. The photo below is how it will appear, notice the “No Data Available”. This is an empty video file.
If you have questions about real-time extraction. Contact our sales engineers or tech support for guidance. Our team is available to help answer questions. Join us next quarter for this ongoing series. We’ll learn about “Locating Extracted Files.”

The team at LENSEC is proud to work with our partner in Texas, Fidelis Cabling. This VAR partner is based in Houston, TX and is a privately-owned company that offers fiber optics, access control, network cabling, and video surveillance solutions.
Established in January 2000, Fidelis builds its reputation by striving to provide the highest quality products and service in the industry. Mike Jaks, President of Fidelis, says, “We have been committed to the philosophy of building long-term partnerships with our client base. We are a company that customizes work based off our clients’ needs. We sincerely care about our customers and care about the security and safety of their employees and property.”
When dealing with troubles in technology it is always best to leave it up to the professionals, and that is Fidelis. This team offers vulnerability assessments and security design as part of their physical security services. Fidelis is committed to helping customers determine the correct solution.
Many access control problems are handled by an amazing team of highly qualified technicians. With over 50 years of combined experience in the access control, there aren’t many problems Fidelis can’t solve.
In security surveillance, Fidelis maintains and troubleshoots video management systems. Upgrades to modern video surveillance systems include technical work on network video, video management software, and video analytics. Fidelis ensures quality work, meeting with potential customers and existing clients to provide the best possible video solution. Upgrade recommendations are based on the individual client’s security needs and concerns along with their budget.
Fidelis has worked with many different brands of video management systems in their history. However, Jaks says, “We’ve found that the product and services Lensec provides fits the Fidelis solution more than any of its competition. With a feature rich product like Perspective VMS and a support team that has always provided unsurpassed technical support, Lensec and Fidelis make a strong partnership.
There are many areas where Fidelis provides expertise. The team at Fidelis is dedicated to customer satisfaction. Fidelis has forged ahead of its competition by taking care of its customers the old fashion way, by standing by what was promised and working until the customer is satisfied.


PVMS PRODUCT HIGHLIGHT
Managing Door Events With Perspective VMS® And Integrated Access Control
By: Mark Wise
Choosing LENSEC and Perspective VMS® opens a big door of opportunity. When the access control system is integrated with PVMS, entrances and exits can be cataloged and reported in the video management software. PVMS provides information on logged events so you have the power to search, find, tag, and share recorded incidents.
PULLING ACCESS CONTROL EVENTS
This is a big plus for customers using an access control product that is integrated with PVMS. When the user is in the PVMS user interface, they can see access control door activity within the event panel. Accessing the door events reveals metadata for the activity and personnel using the doorway.
Access control software doesn’t inherently work in association with a video of activity around a doorway or access control reader. PVMS advances the unified security footprint of the site by leveraging the door events from the access control reader. When the software interfaces work together, then cameras near doorways can show the physical activity of personnel at the time access control events occur.
CONTROLLING ACCESS CONTROL DOORS FROM PVMS
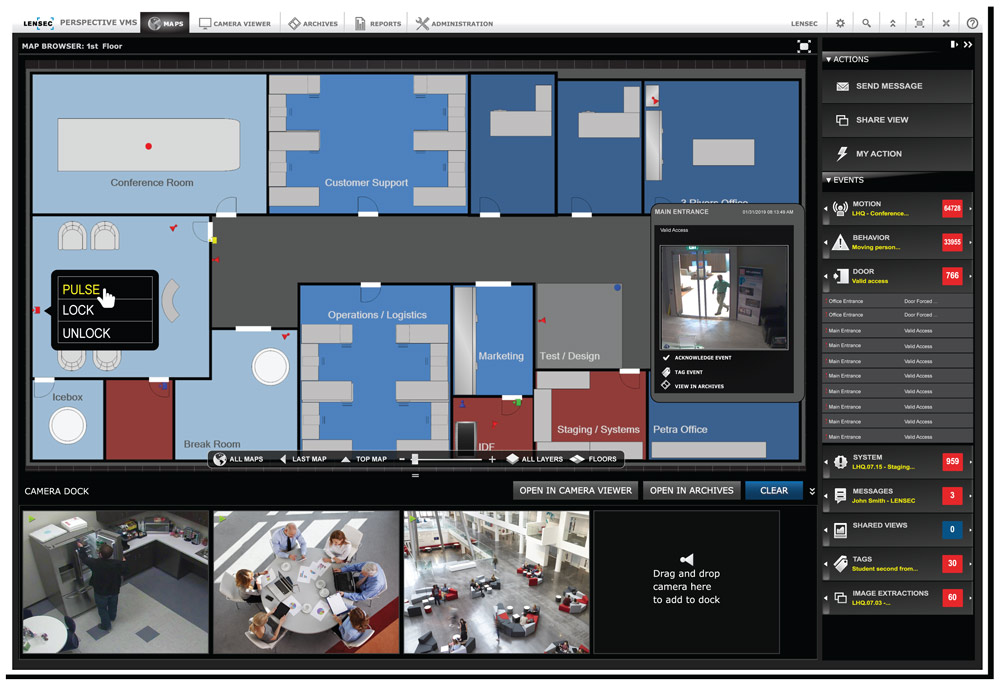
Some integration between PVMS and access control software provides more advanced capabilities. In addition to pulling PACS events into the VMS, users may also be able to control door locks remotely. LENSEC developers have worked with multiple access control companies to send commands from PVMS to the access control hardware. Users can lock, unlock, or pulse doors remotely without needing to be in the access control software. All remote control can be configured to occur within the video management software.
This helps immensely because users can see what’s occurring at a doorway before they send the command to control the door. Now users can actually see who is at the doorway before they release or secure the lock.
SENDING CCTV VIDEO TO THE ACCESS CONTROL SOFTWARE
In a final integration, some access control companies want to pull the video from the VMS into their own user interface. Technically this is possible, but it requires a lot of back end software development by both companies to accomplish the task. A deep integration like this would allow a user to see video from security cameras in either the video management software or the access control software.
LENSEC is pleased to work with several access control technology partners. Our team of PVMS software developers is constantly looking for new ways to bring in software integrations that are helpful for LENSEC VAR partners and their customers.

Criminal Minds
Criminals are looking for easy targets where they won’t get caught. So, they are hunting for places open to the public and minimally staffed. As a result, public locations, such as churches, have been riddled with vandalism and burglaries. However, all is not lost. Experts in physical security know the criminal’s weaknesses and they provide a method that has proven effective in addressing the problem.
Turning the Tables
Criminals move on to other targets when they run into deterrents or obstacles. They don’t want difficulties or interference leading to exposure or arrest. Facility experts and physical security personnel recommend that faith-based organizations eliminate opportunities for criminals. Setting up “Layers of Security” at a site can help stop crime. By using lighting, surveillance cameras, and individuals in strategic positions, leaders at faith-based locations can greatly reduce crime on their property. Understanding how the criminal mind thinks will help. Surveying the property, from the auditorium to outside fence, is key. But how does this work? Assessing the vulnerability of the site with safety and security in mind is the proper approach.

Gates & Parking Areas
Gates and parking lots are the first line of defense. This is the outer layer of security, where observation is the primary approach. During events or weekly services, volunteers or staff are stationed to watch and greet people as they enter the premises. If something seems out of place, they are trained to contact a security administrator or staff member, who monitors, or acts based on a predefined security plan. Attendees want a safe place to be with their family and friends. Having a proper security plan that is properly administered will improve the overall feeling of safety.
Security cameras may be deployed to cover wide areas, but may only be focused on choke points, obvious locations where traffic flows through driveways and/or security gates.
Building Entrances
The second layer of security is comprised of building entrances, walkways, and the perimeter surrounding buildings. Volunteers are positioned here before, during, and after events to greet people as they enter the premises. Making eye contact and offering to help direct an unrecognized visitor may provide insight into a person’s intent.
Security cameras are typically used in this area to help monitor activity and traffic. Live monitoring doesn’t have to be present, but it might be helpful for a security team to keep an eye on a large facility from a control room location. During events, doors are unlocked, but when facilities are closed, access control doors can restrict unauthorized personnel from secure buildings.

Auditoriums & Classrooms
The most secure layer of security is the auditorium and classrooms. When services are underway, trained volunteers and staff may be positioned where they can monitor the grounds and hallways to watch for suspicious activity. Positioning a trained attendant throughout the sessions has proven to reduce suspicious activity and add to the feeling of safety among attendees.
Some faith-based organizations lock entrance doors during the events while keeping life safety and exit strategy protocols in place. Life safety standards call for safe egress without locks in case of emergencies. Cameras in the auditorium may be present and surveillance cameras can be used to monitor parking areas during events. Restricted areas should remain locked with access control to keep curious people from locations that are off-limits.

Security Technology
Good lighting around the property is helpful for deterring criminal activity at night. If you haven’t walked around the grounds and facility at night, you should schedule a night visit to assess the vulnerability of your site. You might discover lights that need to be replaced or secure areas that don’t have enough lighting to provide adequate security.
In buildings and around the grounds, cameras with infrared capabilities are helpful. These cameras provide a nearly invisible illumination over an area that helps the cameras to see the surrounding area – even in the dark. IR cameras are a security staple for surveillance cameras. IR technology really enhances the ability of security personnel to see what’s happening within view of the camera.
Security Integration
A central control system, also known as a Video Management Software (VMS), can improve your security in an easy-to-use interface. It needs to work seamlessly with high-resolution IP cameras on site. Enterprise software, such as Perspective VMS®, can unify your security footprint by integrating access control, security cameras, and other security systems. PVMS uses interactive maps and camera groups to prevent security operators from losing track of suspicious individuals.
As your facility personnel engage in careful security planning, your commitment to the safety of your community will become abundantly clear. LENSEC can help with vulnerability assessments and technology recommendations. Please contact our team of physical security experts. We are behind you 100% in your goal to ensure the safety of your faith-based organization.

LENSEC has just released the latest addition of Perspective VMS®. PVMS Version 4.2.0 is a minor release with some new features, enhancements, and maintenance items. Some highlighted features are as follows:
3RD PARTY SOFTWARE INTEGRATION
• Receive server health alerts from Razberi Technologies appliances
• Pull access control events from WinDSX Events Cast API
• Receive events from Planar Video Wall controllers
• Event Analytic Overlay displays metadata on archive video and images
PTZ SETTINGS – Option to set PTZ presets for camera configuration at the edge and set a timeout for PTZ to return to home position
H.265 VIDEO EXTRACTION HANDLING – Improved handling for H.265 archive video extractions
SYSLOG (SNMP) DEVICE CONNECTION – Communication improved by adding syslog connections for SNMP devices
OTHER ENHANCEMENTS – Additional enhancements to existing features included in the new release version
The full release notes for PVMS Version 4.2.0 are available on the LENSEC website downloads page and the Perspective VMS® product page. In addition, this page is where you can find the latest software download for PVMS v4.2.0.
If you need assistance, please don’t hesitate to contact our support team. Thanks for trusting in LENSEC and Perspective VMS®.

LENSEC Headquarters
3151 Briarpark Drive, Suite 125
Houston, TX 77042 United States
LENSEC.com | +1 (713) 395-0800
Contact Us for a PVMS
Sales Demonstration or
Free 30-Day Software Trial